Monday, Sept 30 2024
Attackers can force Echos to hack themselves with self

By A Mystery Man Writer
Popular “smart” device follows commands issued by its own speaker. What could go wrong?

Internet of things' security introduction for EMS leaders

What to Do When You've Been Hacked

CVE-2023-49291 and More – A Potential Actions Nightmare – Adnan
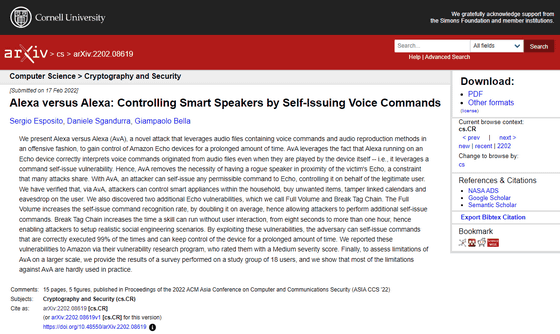
s Alexa reports 'Alexa versus Alexa', an attack method that

Attackers can force Echos to hack themselves with self

Hacking reality
What is a Cyber Attack? Definition and Related FAQs

Human Hacking: Win Friends, Influence People, and Leave Them

Hack Defense
Related searches
- Best Buy: Echo Dot (4th Gen) Smart speaker with clock and

- Echo Plus with built-in Hub 1st Generation – Black

- Echo Show 10 (3rd Generation) 10-inch Smart Display with Alexa Charcoal B07VHZ41L8 - Best Buy

- Echo Dot with Clock (5th Gen, 2022 Release) Compact Smart Speaker with Alexa - Glacier White

- Echo Dot 3rd Generation: A Detailed step-by-step Alexa vital Manual that shows you cool things to do with echo

Related searches
- Ahoy Sailor Hat, Animal Jam Classic Wiki
- Plus Size - Black Lace Cutout Cage Underwire Bodysuit - Torrid
- Skirt Pastel Ombre One Size - Frankies Melbourne* – National

- Back when I had no money to advertise and my entire ad strategy was wearing a black t-shirt I made at a local shop by ironing on an S-P-A
- Dora Line Printed 100% Cotton Baby Boys & Girls Briefs Drawer Inner Underwear Combo Offer

©2016-2024, doctommy.com, Inc. or its affiliates

