Thursday, Jul 04 2024
Layer 8 Hacking - Linking the OSI Model with the NIST Triangle

By A Mystery Man Writer
Layer 8 Hacking can be defined as hacking above and beyond the technical layers; hacking by targeting the user, the business processes, or the organization i

Computer Systems Security: Planning for Success

Phase I: CSDS as an Emerging Profession—Diagnostic Literature

Blog – Cyber Physical Risk Academy

Why Layer 8 Is Great

Electronics, Free Full-Text
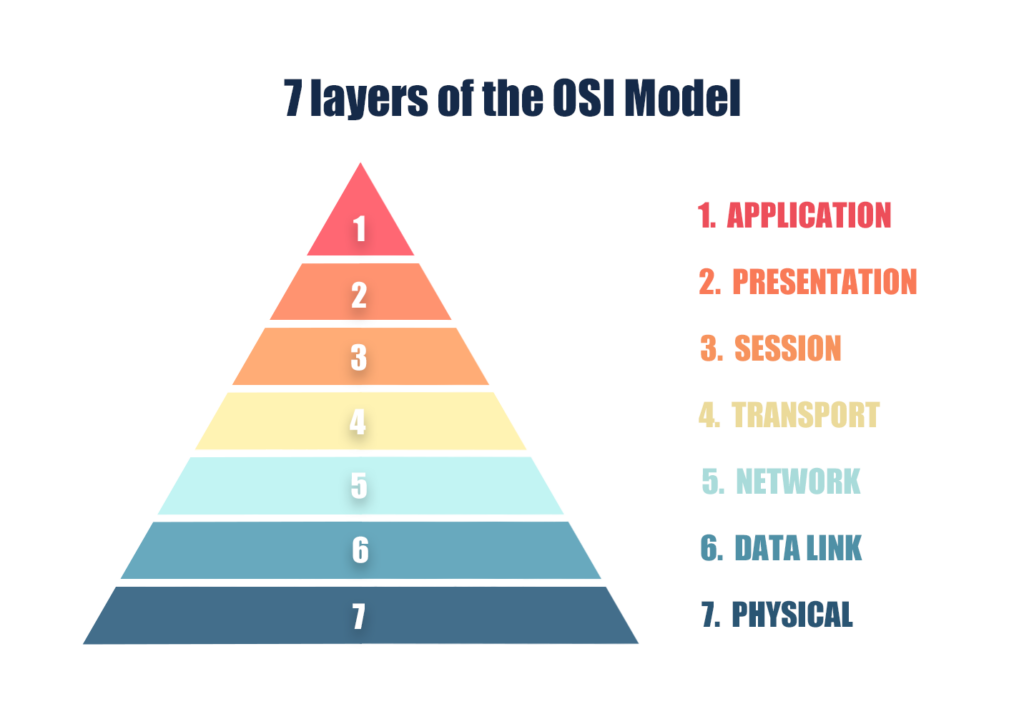
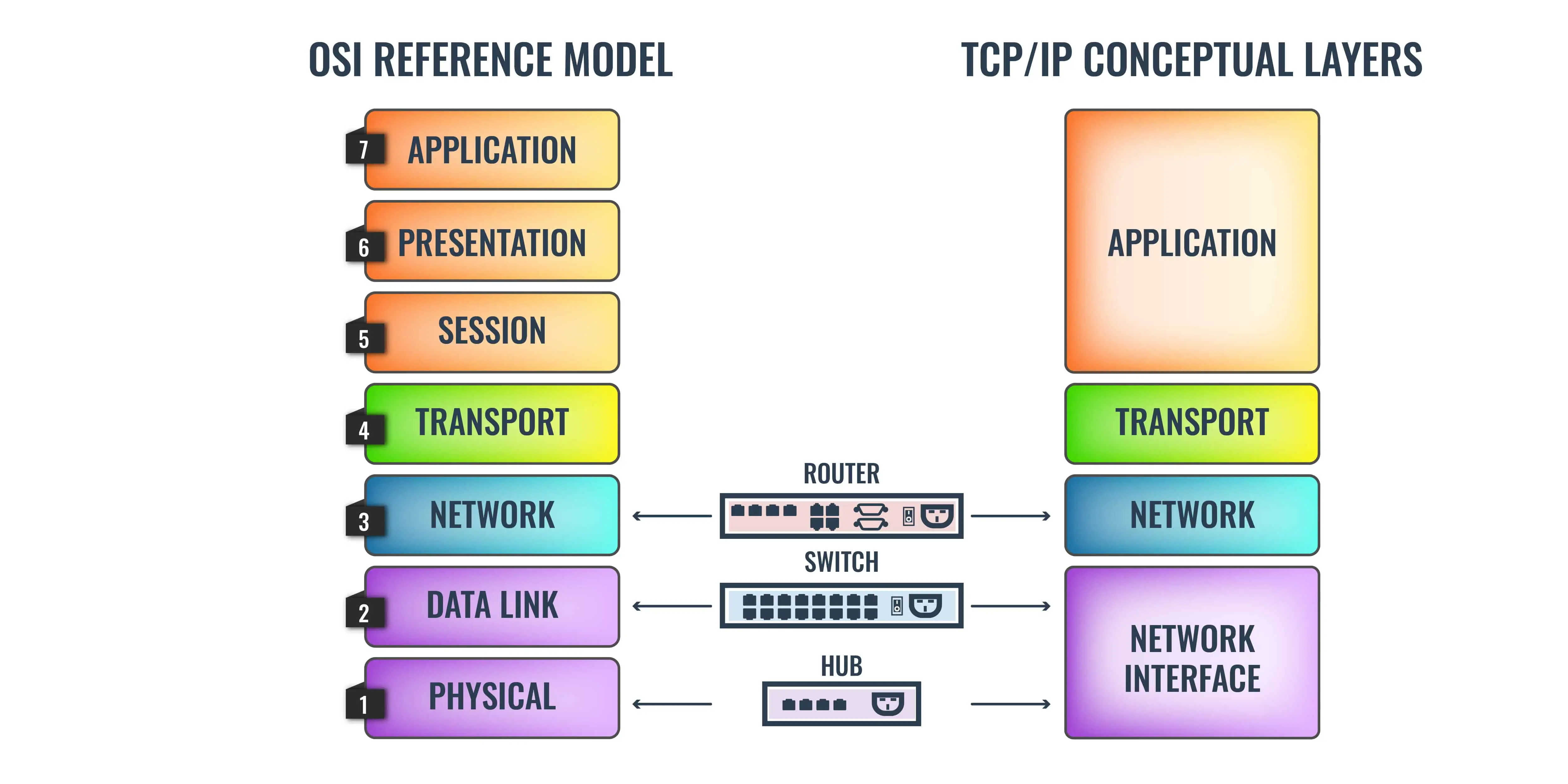
OSI model vs TCP/IP model - What's the Difference & Networking Basics
The OSI Model Explained: Handy Mnemonics to Memorize the 7 Layers
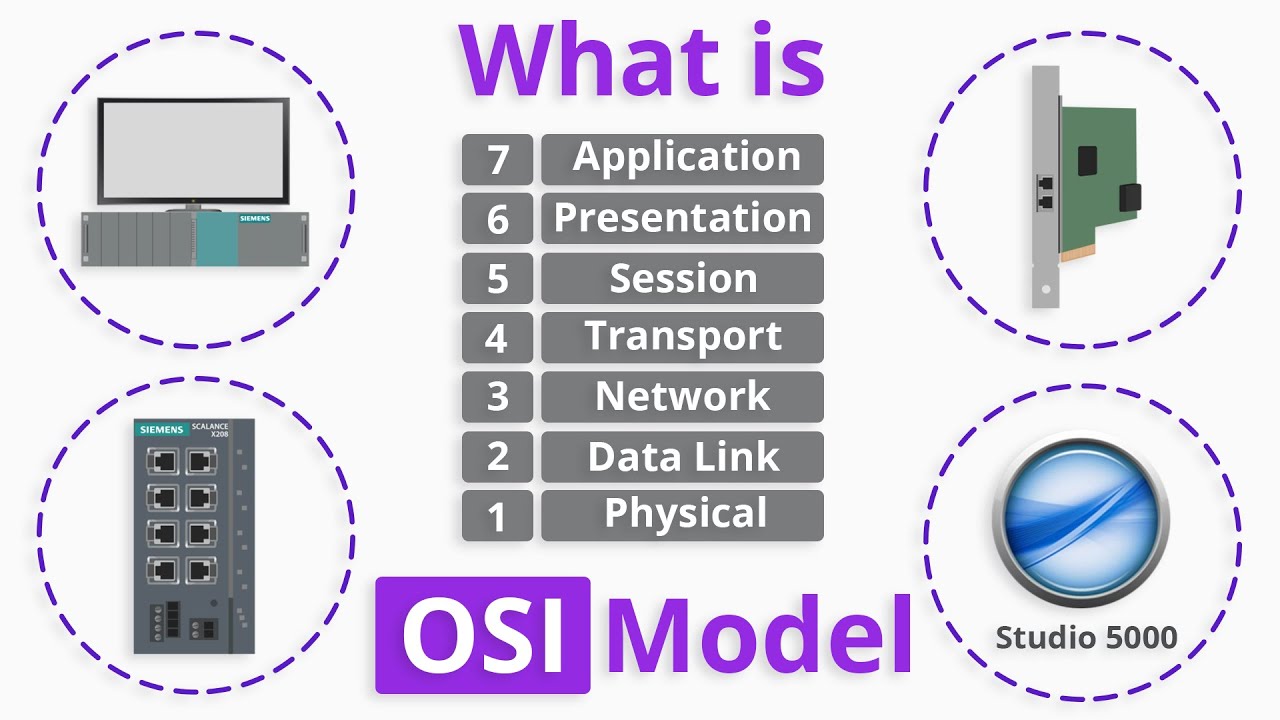
What is the most important layer of the OSI model during Cyber

Algorithm of our proposed IDS.
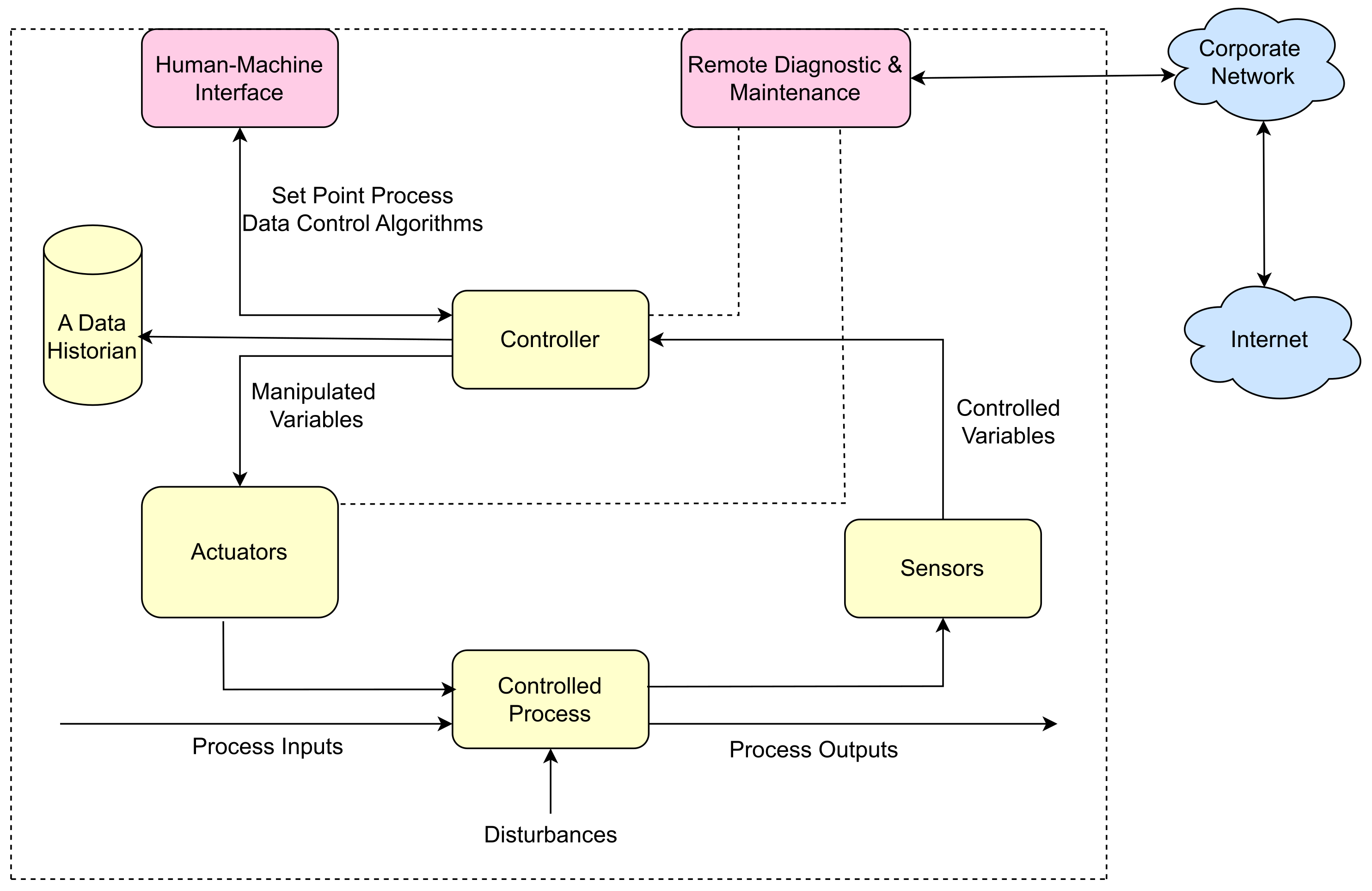
Sensors, Free Full-Text
Related searches
Related searches
- Bad Brains Records

- YYDGH Lace Bras for Women Plus Size Comfort Seamless Print

- Polly Jersey Dress, Womens Dresses

- Paw Prints, Blue, Pawprints, Paws, Dog, Puppy, Pup, Mutt, Canine, Print, Car, Auto, Wall, Locker, Laptop, Notebook, Netbook, Vinyl, Sticker, Decal, Label, Placard, (Blue) : Tools & Home Improvement

- Control Thong

©2016-2024, doctommy.com, Inc. or its affiliates




